Rangecast FAQ
[FAQ-1121] Windows Defender falsely reporting Rangecast software as malware
Page Type: SOLUTION
OVERVIEWAntivirus systems (such as Microsoft Defender) sometimes falsely identify application software as containing a virus. When this happens, critical files needed for the Rangecast application may be removed (quarantined or deleted), with the result that the software no longer works. The exact symptom depends on which files are zapped by the antivirus system, and when it happens. This is resolved by releasing the critical files from quarantine, or replacing these files in the SENDER folder from a fresh download of the Rangecast installation package.
TESTThe best way to determine whether your antivirus system has removed or quarantined components of the Rangecast system is to locate a report page inside your antivirus system listing actions taken against suspected threats, and review the report to see if any files in the Rangecast application (usually in a folder named SENDER on the desktop) were identified as suspicious files.
METHODWhile it is theoretically possible for any software application to be replaced with infected files that contain malware, our experience has been that false detections happen on occasion (situations where a zealous antivirus system falsely identifies Rangecast as a suspected threat), while there has never been an actual infection of Rangecast software or packages with any malware or virus.
It is obviously sensible to proceed with caution whenever an antivirus system tags a file as suspected malware, and we understand if a customer wants their IT department to review a PC before resuming Rangecast operations on the PC. However, given the observed frequency of false positives, we also believe that it's sensible to recognize that -- even when Rangecast is reported as suspected malware -- the odds of this being true are still relatively close to zero, so there is no great cause for alarm.
REFERENCEEXAMPLE - INCIDENT REPORT
The following screenshots were captured on 7 December 2016 from a PC running Rangecast feed site software. In the final image, Microsoft notes that their automated threat detection service had incorrectly flagged legitimate software as having this virus on the previous day.
This first screenshot shows the symptom presented to the user in this particular incident. In similar situations in the future, the symptom will likely be different; how the Rangecast software fails will depend on which critical file is removed.
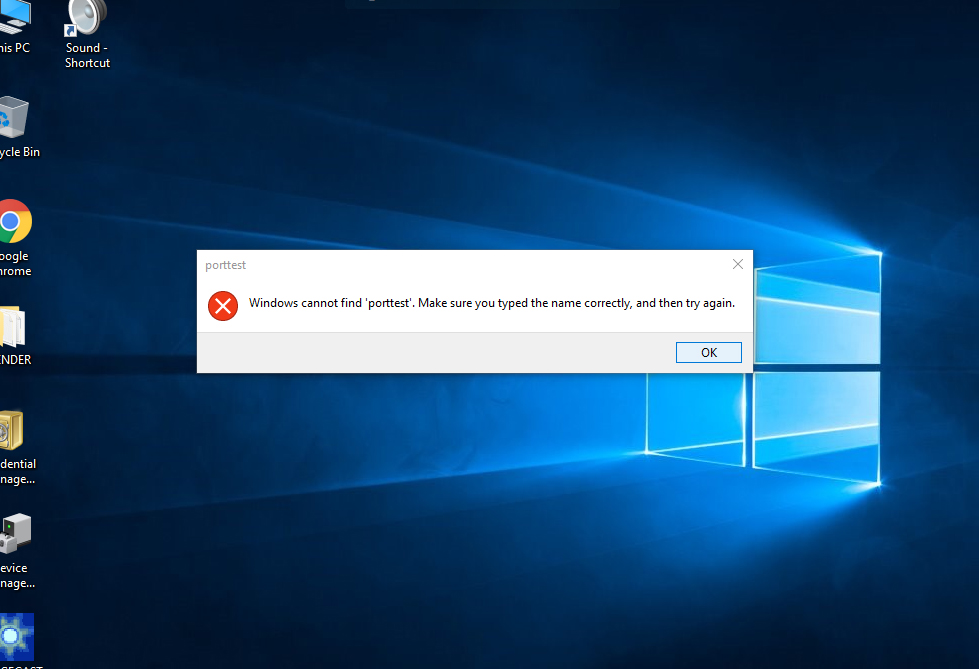
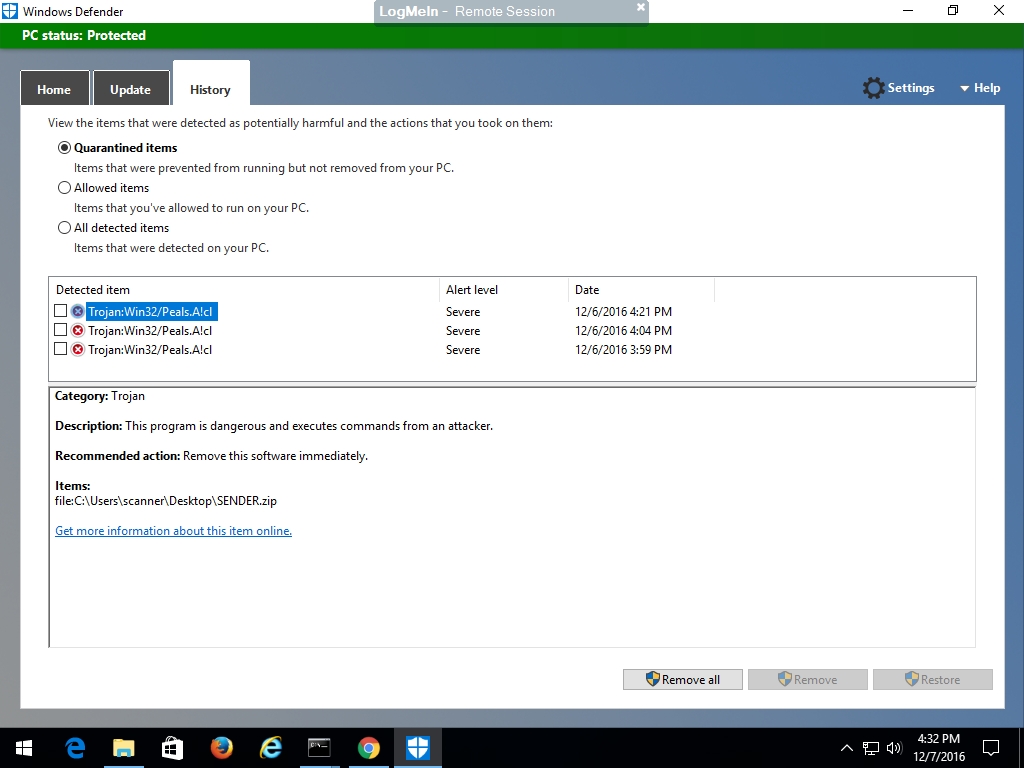
The Windows taskbar included an alert for pending system messages, and clicking that showed a report mentioning Windows Defender action against suspicious files
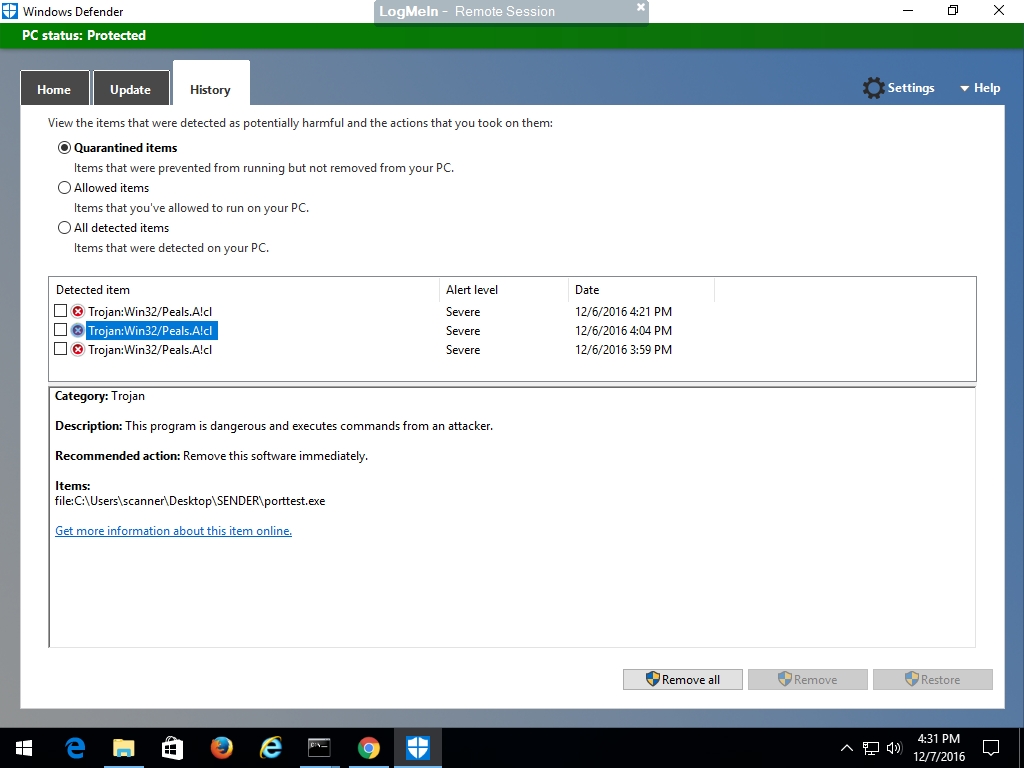
Clicking into Windows Defender to examine the details, several files were reported to be infected with a specific virus. First, Windows Defender removing the critical file "portttest.exe" is what caused the symptom shown above on the customer desktop.
In addition, Rangecast Defender removed two DLL files (php_bcompiler.dll and php_winbinder.dll) that are part of the software library used by several components of Rangecast, including porttest and multisync. These are standard library files used with the PHP programming language, and are not specific to Rangecast.
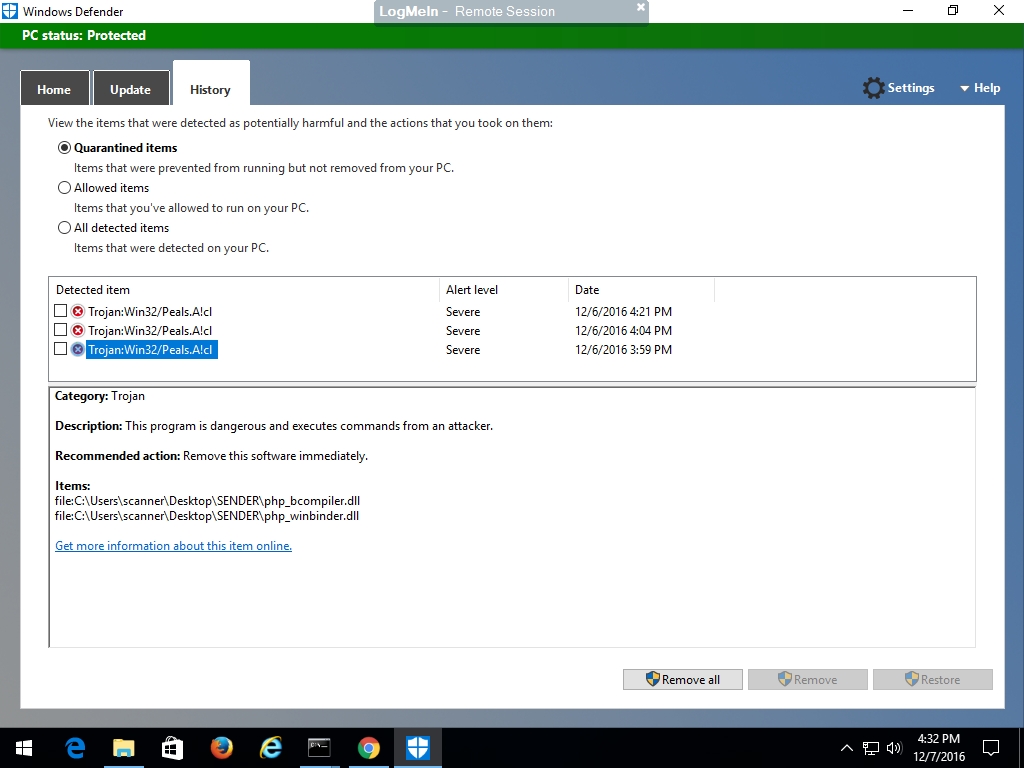
Finally, Windows Defender also took action against the Rangecast installation package "sender.zip" (which includes fresh copies of porttest.exe and the two DLL files). We don't know if this was left on the PC when the software was originally installed, or was downloaded by someone attempting to fix the problem by re-installing the application.
Clicking on the link "Get more information about this item online" brought up a Microsoft webpage describing the suspected threat posed by these files. At the bottom, the website notes that "an incorrect detection for our cloud-based protection for Trojan:Win32/Peals.A!cl was identified and immediately fixed."
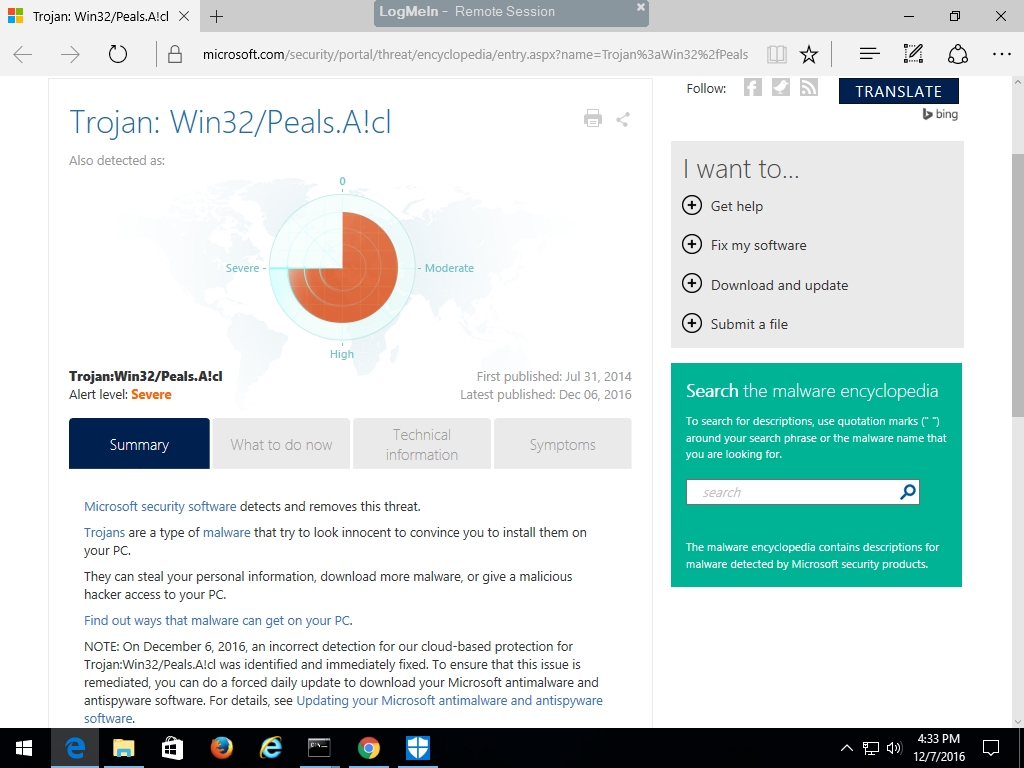
We understand this to mean that Windows Defender incorrectly zapped critical files from working applications, including Rangecast, due to a false detection in their automated threat detection system. This happens sometimes, since antivirus systems sometimes must act on automatic algorithms without human oversight, or verification that a suspicious file is actually a threat.
When this happens to an installation of Rangecast, the two most common reasons seem to be either
(a) the network behavior of Rangecast is deemed suspicious -- frequent automated upload of small files to a cloud service, or
(b) the Rangecast application uses standard libraries that are part of the PHP programming language, and when a threat detection system finds real malware written in PHP on an unrelated PC (no connection to either Rangecast or the customer), the antivirus provider sometimes tags all files found in the infected application as suspicious -- including standard software library files (not infected) used by numerous Windows applications, resulting in a false report of infection in any application (including Rangecast) written in this version of PHP. (This would be similar to reporting Microsoft Word as a virus, because someone had written malware that infected a Word document.)
CITATIONSINDEX
- [FAQ-1280] INDEX - Radio Receiver Site (feed site) - Setup problems
Images shown - [block]





